Login required to access some wiki spaces. Please register to create your login credentials
|
34. As explained in the previous chapter, managing the proper application of policies to different classes of data (or information in general) is rather complex. Statistical organizations have therefore tried to simplify things. One of the measures organizations traditionally have taken is to turn themselves into "strongholds", with "walls" and "mounts" around them. Inside, the data was considered to be safe, and usually, all data was treated in more or less the same way, i.e. no differentiation of policies for different classes. And then they built the equivalents of gates and drawbridges to allow data to flow into and out of their stronghold in manners that could be controlled.
35. Nowadays, we find that these traditional measures no longer are adequate[1]. More and more, we need closer interaction with external parties, both providers and consumers. And so, we need to allow these external parties inside our strongholds and we also want to participate (and use our data) outside, in the cloud or even on systems controlled by our allies. But still, we need to be able to control the flow of information into and out of areas under the control of separate organizational units. So there still is a need for "toll gates". Exchange Channels provide such mechanisms.
36. GSIM defines an Exchange Channel as “An abstract object that describes the means to receive (data collection) or send (dissemination) information”. GSIM is referring to the information object describing the “real thing”, i.e. the actual Exchange Channel being “the means to receive or send information”. CSDA is concerned with the latter. Contrary to GSIM, CSDA does not restrict Exchange Channels to Data Collection and Dissemination (in GSBPM terms), as will be explained in the following.
37. As explained before, the original purpose of channels is to control the flow of information in or out of an area of control, i.e. an area controlled by some power (e.g. an organizational unit). Channels are owned and provided by the one responsible for the controlled area. But they are used by those that want (or need) to provide or access information. They are the points of exchange between different areas of responsibility. And thus they are the natural places for controlling the flow. More and more, however, these touchpoints also become the focus of user friendliness, and therefore channels must provide alternatives to consumers and providers. Alternatives that must fit the needs and concerns of those users. As we will see further on, channels have several responsibilities or tasks related to this control of flow of information.
38. There are two kinds of Exchange Channels: those that disclose information sources and those that allow consumers to access the information assets (treasures) of the statistical organisation. For ease of reference, we’ll call the first kind “input” and the second kind “output”. By making information out of sources accessible through “input” channels, that information is thereby considered valuable enough to be treated as an asset.
39. It should be stressed here that information sources and information consumers not necessarily are meant to be “external to the organisation”. They are “external to the sphere of control” exercised by the statistical organisation (or one of its agents[2]) on all its information assets. Information is placed under such control by opening up an input channel to that information. Information leaves such control by allowing it to “exit” through one of the output channels. The collection of information under such control is also referred to as “the pool”. It is important to understand that "the pool" is a concept, denoting the collection of information, not necessarily a storage pool. And most certainly not a centralised storage. As will be explained in a later chapter, the information considered "in the pool" may never actually be physically stored there, but only pass through from some input channel directly to some output channel. Still, this information is considered "under control".
40. The next figure schematically shows these concepts:
Figure 1: Pool & Channels
41. Equally important is to understand that even the channels themselves, and (part or whole) of “the pool” may be located outside of the premises of the statistical organisation. That is, they may be located “in the cloud”, or even on the premises of some other (private or public) organisation, as long as the statistical organisation has sufficient control to ensure that its interests in terms of protection of the information assets is safeguarded.
42. Exchange channels are also the organisation’s interfaces to the outside world. And because of that, they need to be flexible enough to follow the developments in that outside world. New technologies that open up new opportunities, new demands from providers or consumers, new types of information that require new ways of connecting, these are all examples of developments that channels must be able to adapt to. To put it in other words: exchange channels must be replaceable, in a “plug and play” manner. And they must provide a variety of different interfaces to the outside world in order to satisfy the variety of different requirements. On the inside, however, channels should present a standardized interface. How else can they be “plug and play”, if every new channel requires changes to the internal systems?
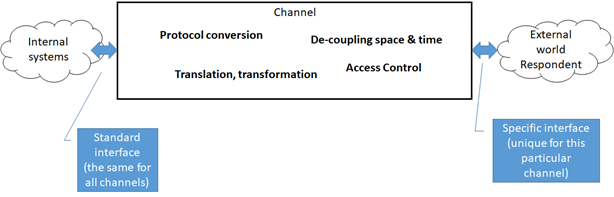
43. Turning to the tasks of an exchange channel, it is obvious that its main task is to transport (“channel”) information. And, as we have already seen, it must be able to present some interface on the outside, and (most likely another) one on the inside. Part of an interface is a protocol, so a channel is also a protocol converter. In addition, a channel must be able to bridge the distance (both in space and in time) between external source or consumer and the internal side. Furthermore, a channel must be able to reliably establish the identity (authenticate) and the authorization of the external party (Access Control). And lastly, the channel may need to do translation, in some cases even natural language translation, but more likely transformation of format. The channel will need some internal process, to control its behaviour. In most cases, in the traditional data collection, this is done through training of interviewers and by providing questionnaire instruments. Both are examples of “configuring” the channel for specific surveys. The next figure shows the necessary capabilities of a generic channel.
Figure 2: Generic Exchange Channel
44. More details about the internal workings of Exchange Channels can be found in the Annex: Examples of Exchange Channels.
[1] Since 2003, the Jericho Forum (merged with The Open Group Security Forum in 2014) is working on this topic[1], called “de-perimeterisation”.
[2] For the definition of “agent”, ref GSIM